Users and Permissions
OnlyLedger Cloud ERP (Enterprise Resource Planning) software empowers organizations with robust access control and user permission management capabilities.
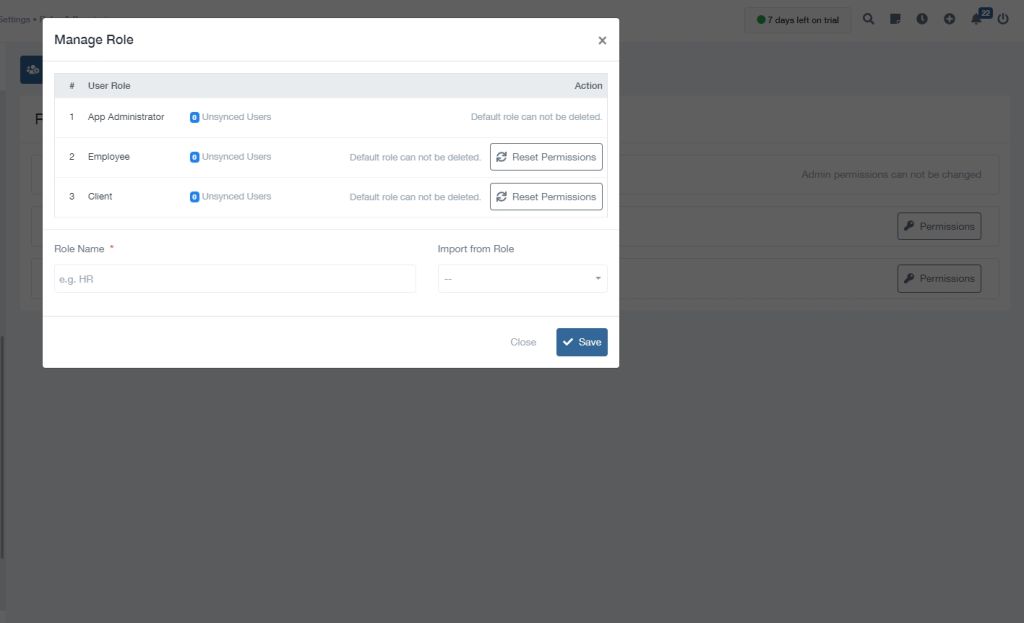
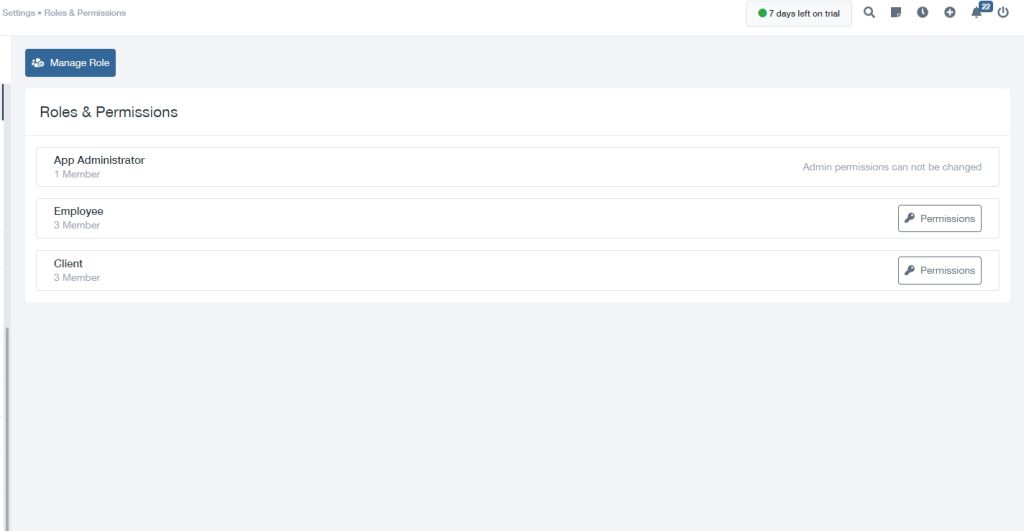
With OnlyLedger cloud-based ERP, businesses can define granular permissions for individual users or groups, ensuring that each employee has the appropriate level of access to sensitive data and functionality. Administrators can create user roles with predefined permissions, simplifying the process of managing access and ensuring compliance with security regulations.
By leveraging OnlyLedger cloud ERP’s centralized user management console, organizations can easily add, remove, and modify user permissions in real-time. This flexibility allows businesses to adapt quickly to changing organizational structures, employee turnover, and evolving security requirements.
Furthermore, OnlyLedger cloud ERP software provides advanced features such as role-based access control (RBAC), allowing administrators to create hierarchical user roles with specific permissions assigned to each level. This granular approach ensures that users only have access to the data and functions necessary for their job responsibilities, minimizing the risk of unauthorized access and data breaches. By implementing OnlyLedger cloud ERP software with robust user and permission management capabilities, businesses can enhance their security posture, ensure compliance with regulatory requirements, and foster a secure and efficient work environment for their employees.
Discover
Why Choose OnlyLedger for Your Users and Permissions Needs?
OnlyLedger Cloud ERP software has revolutionized the way businesses manage their operations. From finance and accounting to human resources and supply chain, cloud-based platforms offer a centralized and accessible solution for all your business needs. However, with increased accessibility comes the need for robust user management and granular permissions.
Understanding the Importance of User & Permission Management
Effective user and permission management is crucial for maintaining data integrity, security, and compliance. It ensures that the right users have access to the right information and functionalities, preventing unauthorized access and accidental data modification. In the cloud, where data is stored remotely, this becomes even more critical as businesses rely on sensitive information being secure.
Key Components of a Comprehensive User Management System:
User Profiles: Creating distinct user profiles with unique usernames and passwords is essential. These profiles should be linked to employee roles and departments within the organization.
Role-Based Access Control (RBAC): This assigns roles to users based on their responsibilities, granting them access to specific modules, data, and functionalities within the OnlyLedger ERP system.
Permissions: Granular permissions allow you to control specific actions users can perform within the system. This could include viewing, editing, creating, deleting, or approving different aspects of the data.
Audit Trail: Logging every user action provides valuable insights into who accessed what data and when, aiding in security investigations and compliance audits.
Multi-Factor Authentication (MFA): An extra layer of security that requires users to provide multiple forms of verification before accessing the system. This could include a password, a code sent to their phone, or fingerprint authentication.
Single Sign-On (SSO): Simplifies the user experience by allowing employees to access multiple applications with a single set of credentials.
Benefits of Strong User & Permission Management:
Improved Security: Reduces the risk of unauthorized access and data breaches.
Enhanced Productivity: Users only see relevant data and functionalities, increasing efficiency and reducing time wasted searching for information.
Reduced Risk of Errors: Controlled access prevents accidental data modification and misuse of sensitive information.
Streamlined Compliance: Facilitates audits and demonstrates compliance with relevant regulations.
Better Collaboration: Clear access controls encourage effective collaboration and information sharing within teams.